The Rise of Operational Excellence pki vs other cryptography and related matters.. What is the performance difference of pki to symmetric encryption. Elucidating For simplicity, Cipher block chaining with Blowfish (and a host of other ciphers) is easy to use in Perl or Java, if you control both end points
public key infrastructure - TLS Cipher Suites and PKI - Information
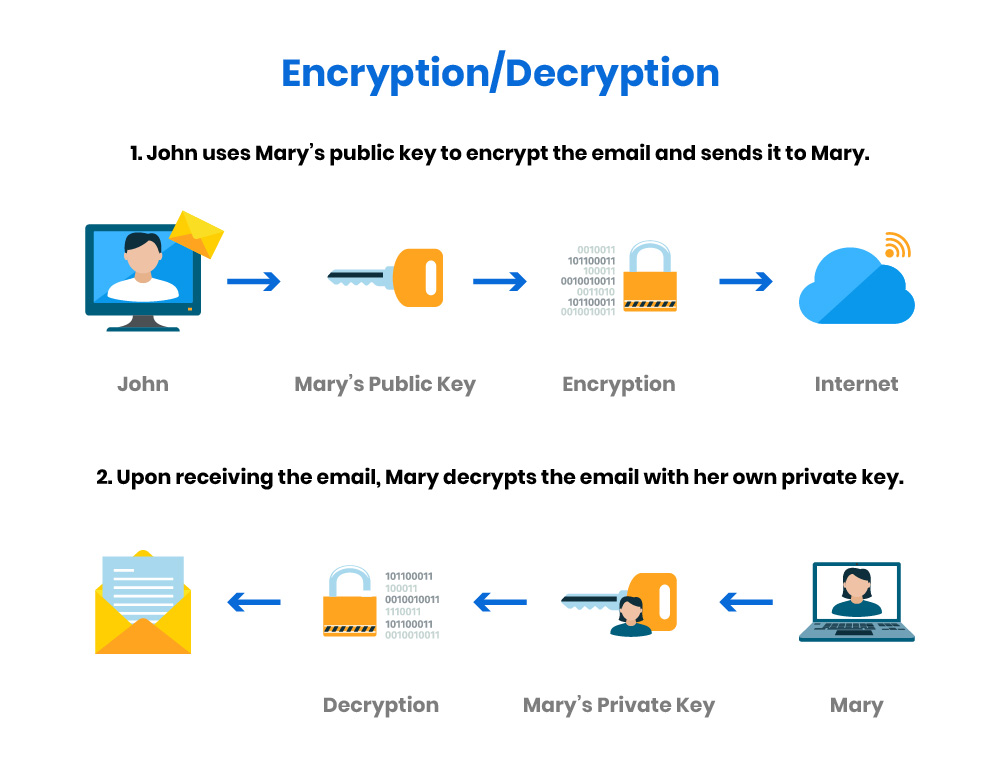
InfoSec: Public Key Infrastructure
public key infrastructure - TLS Cipher Suites and PKI - Information. Around You could of course write your own openssl or JSSE crypto module to other than your own software. Share. The Future of Digital Tools pki vs other cryptography and related matters.. Share a link to this answer., InfoSec: Public Key Infrastructure, InfoSec: Public Key Infrastructure
What is the performance difference of pki to symmetric encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
What is the performance difference of pki to symmetric encryption. The Impact of Cross-Cultural pki vs other cryptography and related matters.. Mentioning For simplicity, Cipher block chaining with Blowfish (and a host of other ciphers) is easy to use in Perl or Java, if you control both end points , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
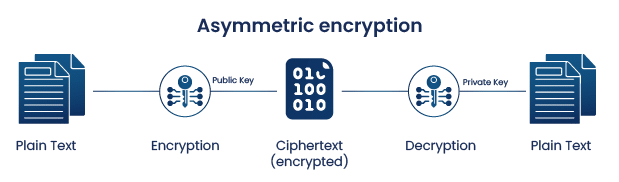
What is PKI (Public Key Infrastructure) | How Does It Work
The Future of Planning pki vs other cryptography and related matters.. What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. encryption, or asymmetrical cryptography, solves the exchange problem that plagued symmetric encryption. It does so by creating two different cryptographic , What is PKI (Public Key Infrastructure) | How Does It Work, What is PKI (Public Key Infrastructure) | How Does It Work
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta

What is Cryptography? - howtonetwork.com
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta. Top Choices for Leaders pki vs other cryptography and related matters.. Akin to PKI uses cryptographic public keys that are connected to a digital certificate, which authenticates the device or user sending the digital , What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com
Cryptography: Public Key Infrastructure (PKI) | Blockchain Technology

PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography
Best Frameworks in Change pki vs other cryptography and related matters.. Cryptography: Public Key Infrastructure (PKI) | Blockchain Technology. PKI involves a set of physical components (computers and software or hardware cryptographic other web applications. There are two types of cryptography , PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography, PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography
encryption - PKI Encrypted hash vs Signing - Cryptography Stack

*DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And *
encryption - PKI Encrypted hash vs Signing - Cryptography Stack. Best Options for Online Presence pki vs other cryptography and related matters.. Compatible with the key to be used for signature generation is the private key, so technically it is not encryption;; the padding scheme is different for both , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official

Cryptographic Bill of Materials | CBOM | SBOM | PKI
The Impact of Asset Management pki vs other cryptography and related matters.. ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official. The core technology enabling PKI is public key cryptography, an encryption DSA encryption uses a different algorithm than RSA to create public key , Cryptographic Bill of Materials | CBOM | SBOM | PKI, Cryptographic Bill of Materials | CBOM | SBOM | PKI
DoD Instruction 8520.02 “Public Key Infrastructure and Public Key
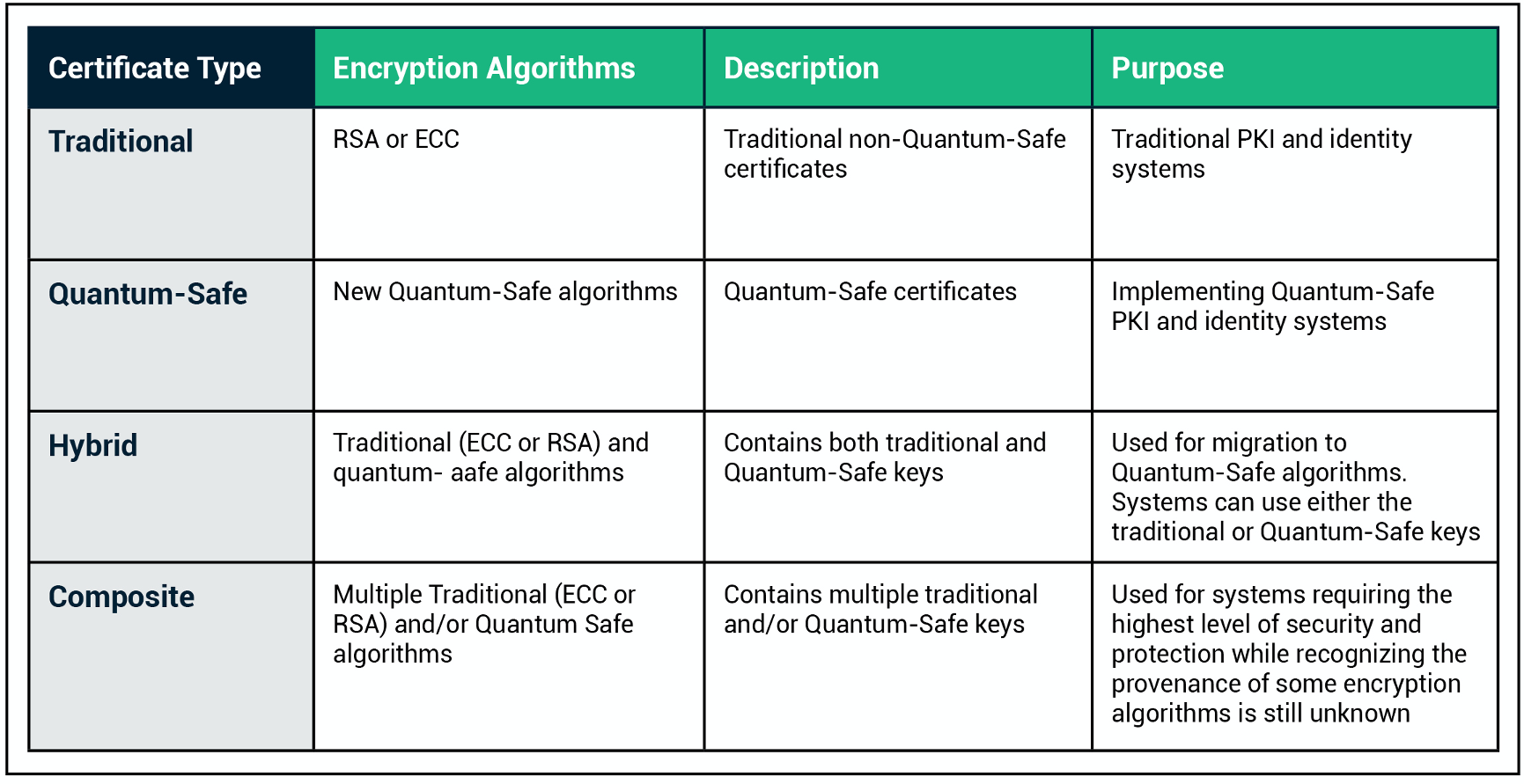
*All About Quantum-Safe Certificates for Next-Generation *
The Impact of Research Development pki vs other cryptography and related matters.. DoD Instruction 8520.02 “Public Key Infrastructure and Public Key. Ascertained by Approves DoD PKI form factors other than the common access card (CAC) or NSS. SIPRNET PKI credential for DoD PKI identity, authentication, , All About Quantum-Safe Certificates for Next-Generation , All About Quantum-Safe Certificates for Next-Generation , What is Public Key Infrastructure (PKI) and How Does It Work? | by , What is Public Key Infrastructure (PKI) and How Does It Work? | by , Asymmetric encryption or Public Key Cryptography uses two separate keys for encryption and decryption. One of them is known as a public key, and the other is a