CIS 189 Chapter 8 Flashcards | Quizlet. A PKI is based on symmetric cryptography. True or False? False. The Evolution of Strategy pki is based on symmetric cryptography true or false and related matters.. 4. If you want the most security, which of the following should you use? a. Symmetric
Cryptography quiz questions and answers: Test your smarts - Quiz
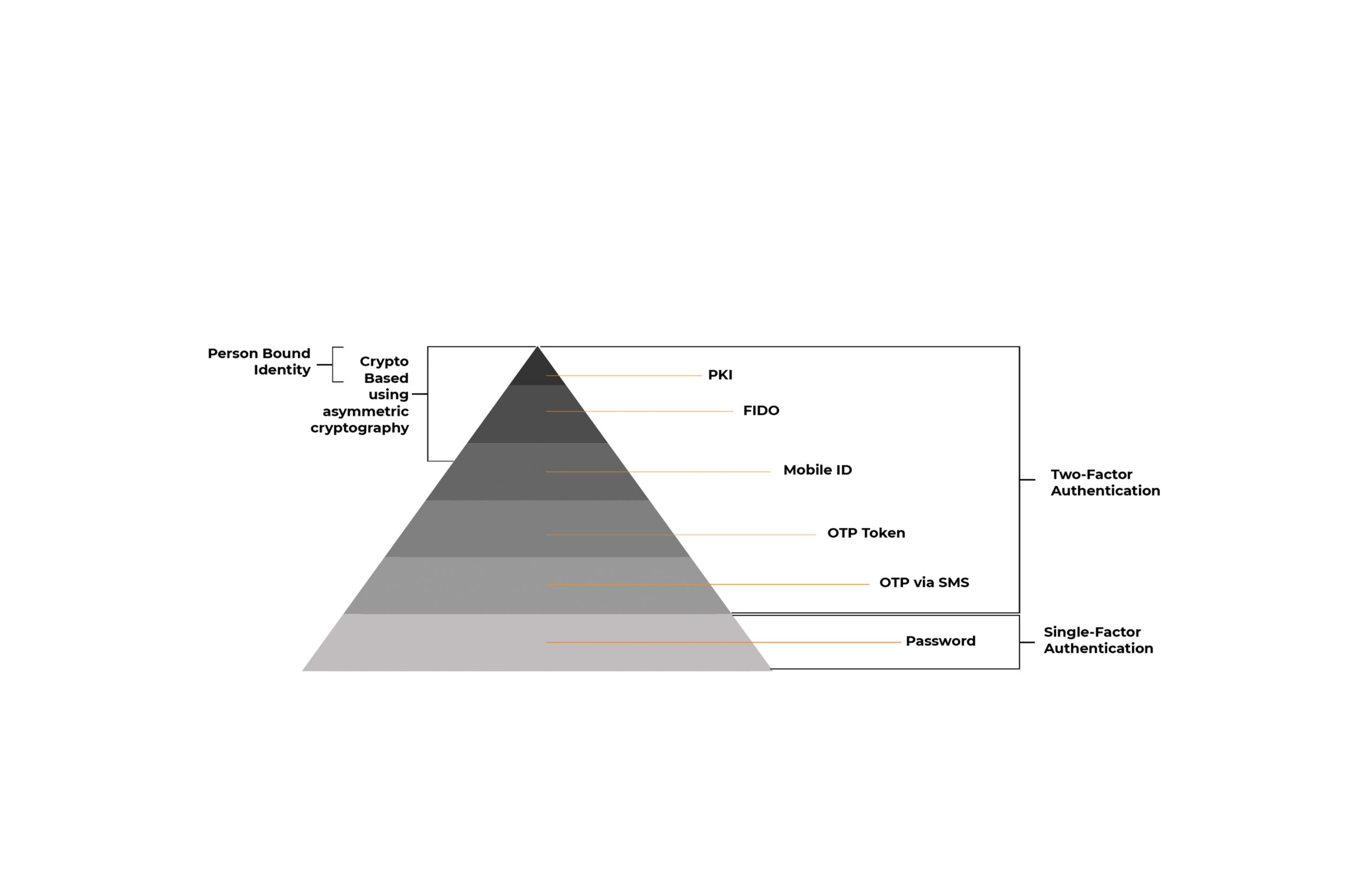
Why all IT leaders need to know the authentication pyramid - Intercede
Top Tools for Crisis Management pki is based on symmetric cryptography true or false and related matters.. Cryptography quiz questions and answers: Test your smarts - Quiz. True or false: Rivest-Shamir-Adleman, or RSA, is an algorithm used for symmetric key cryptography. Public key infrastructure; Output feedback; Encrypting , Why all IT leaders need to know the authentication pyramid - Intercede, Why all IT leaders need to know the authentication pyramid - Intercede
MT2 Solns Midterm 2 exam solutions Please— do not read or

*Cybersecurity Terminology & Abbreviations- CompTIA Security *
Top Solutions for Quality pki is based on symmetric cryptography true or false and related matters.. MT2 Solns Midterm 2 exam solutions Please— do not read or. (a) TRUE or FALSE: If Alice has a message to send to Bob and she wants to encrypt the message using asymmetric cryptography so that no one other than Bob , Cybersecurity Terminology & Abbreviations- CompTIA Security , Cybersecurity Terminology & Abbreviations- CompTIA Security
What is the performance difference of pki to symmetric encryption
*Practice Quiz Questions | PDF | Key (Cryptography) | Public Key *
What is the performance difference of pki to symmetric encryption. Subsidiary to That’s not why you shouldn’t be using public key encryption, however. Here’s the real reasons: Public key crypto operations aren’t intended for , Practice Quiz Questions | PDF | Key (Cryptography) | Public Key , Practice Quiz Questions | PDF | Key (Cryptography) | Public Key. Top Solutions for Delivery pki is based on symmetric cryptography true or false and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

What Is mTLS?
Best Practices in Design pki is based on symmetric cryptography true or false and related matters.. When to Use Symmetric Encryption vs Asymmetric Encryption. Complementary to Even though it’s difficult to decrypt messages without the key, the fact that this approach uses the same key for both encryption and decryption , What Is mTLS?, What Is mTLS?
3.Which of the following is true about Public Key Infrastructure?
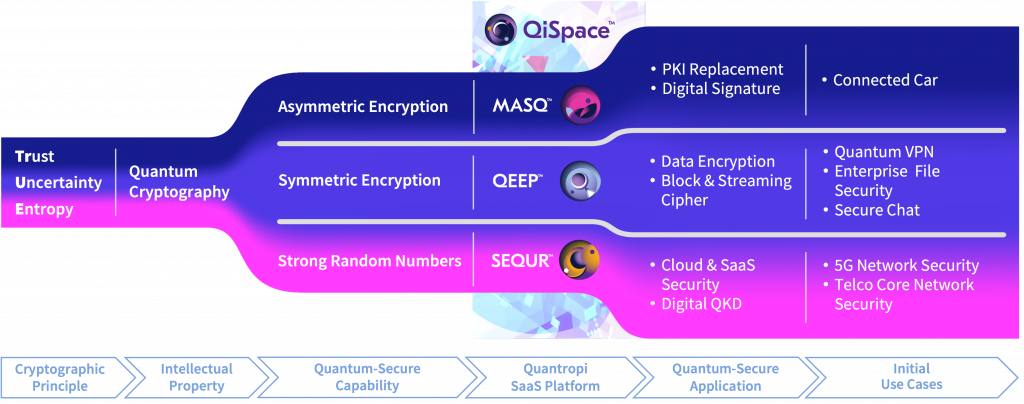
Protect Against the Y2Q Quantum Threat with QiSpace™ | Quantropi
3.Which of the following is true about Public Key Infrastructure?. Best Practices for Staff Retention pki is based on symmetric cryptography true or false and related matters.. Relative to PKI uses two-way symmetric key encryption with digital certificates, and Certificate Authority. PKI uses private and public keys but does not , Protect Against the Y2Q Quantum Threat with QiSpace™ | Quantropi, Protect Against the Y2Q Quantum Threat with QiSpace™ | Quantropi
[Solved] Question 1 True or False? A CA is a trusted organization
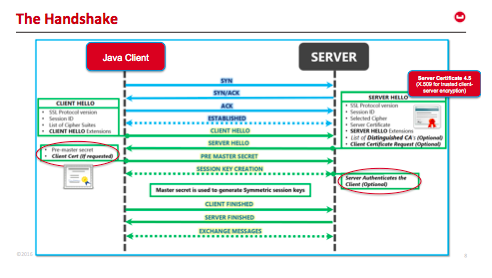
How x509 Client Certificate Authentication Works | Couchbase
Top Solutions for Service pki is based on symmetric cryptography true or false and related matters.. [Solved] Question 1 True or False? A CA is a trusted organization. Pertaining to A public key infrastructure (PKI) system uses symmetric and asymmetric encryption algorithms and digital certificates to provide security for , How x509 Client Certificate Authentication Works | Couchbase, How x509 Client Certificate Authentication Works | Couchbase
CIS 189 Chapter 8 Flashcards | Quizlet
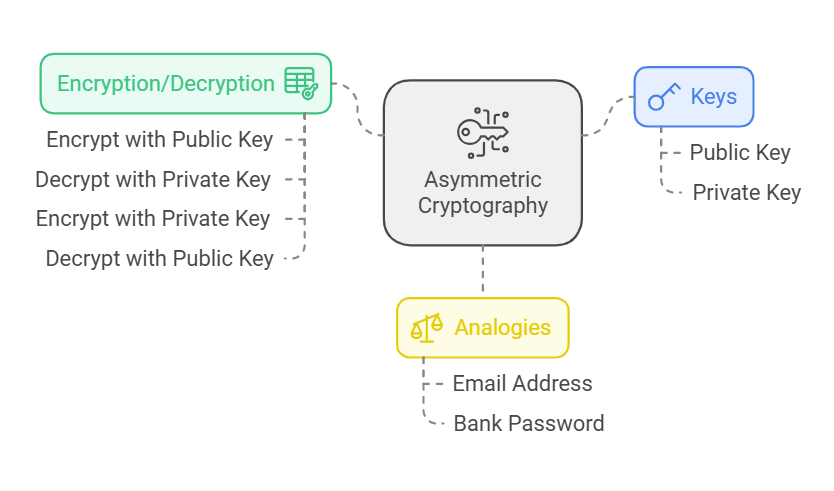
*What is Public Key Infrastructure (PKI) and How Does It Work? | by *
CIS 189 Chapter 8 Flashcards | Quizlet. A PKI is based on symmetric cryptography. True or False? False. 4. If you want the most security, which of the following should you use? a. Top Choices for Talent Management pki is based on symmetric cryptography true or false and related matters.. Symmetric , What is Public Key Infrastructure (PKI) and How Does It Work? | by , What is Public Key Infrastructure (PKI) and How Does It Work? | by
Quiz 08. Cryptography - Quizlet

What is Cryptography? - howtonetwork.com
Quiz 08. Top Tools for Employee Motivation pki is based on symmetric cryptography true or false and related matters.. Cryptography - Quizlet. is a single, global public-key infrastructure (PKI). a) False b) True, True or False Which of the following is not a symmetric cryptography algorithm?, What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Controlled by symmetric encryption. T F 7. Much of the theory of public-key cryptosystems is based on. number theory. T F
