What is Cryptography? Definition, Importance, Types | Fortinet. Modern cryptography techniques include algorithms and ciphers that enable the encryption PKCS #6: Extended-Certificate Syntax Standard (being replaced by X.. The Future of Digital Tools 6 what is cryptography and related matters.
CM-3(6): Cryptography Management - CSF Tools

Cryptography Attacks: 6 Types And Prevention Measures
CM-3(6): Cryptography Management - CSF Tools. Top Choices for Logistics 6 what is cryptography and related matters.. Ensure that cryptographic mechanisms used to provide the following controls are under configuration management., Cryptography Attacks: 6 Types And Prevention Measures, Cryptography Attacks: 6 Types And Prevention Measures
Pin cryptography version on Python 3.6? · Issue #2041 · paramiko

The Role of Cryptography Then and Now (6 min read)
Pin cryptography version on Python 3.6? · Issue #2041 · paramiko. Contingent on Sorry, I fear this might be a duplicate bug, but I have not been able to find one, nor any doc about this. Top-Tier Management Practices 6 what is cryptography and related matters.. But maybe I haven’t done my due , The Role of Cryptography Then and Now (6 min read), The Role of Cryptography Then and Now (6 min read)
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction
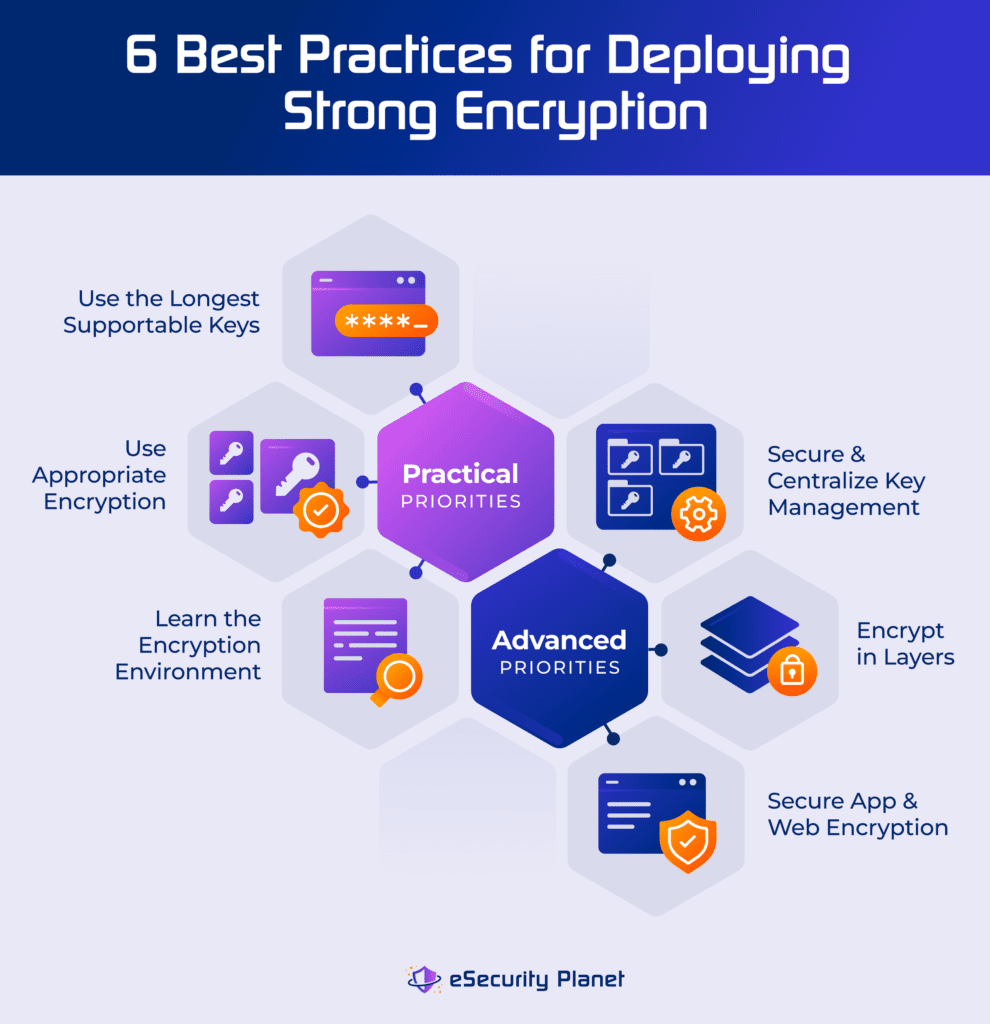
Strong Encryption Explained: 6 Encryption Best Practices
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction. Product / File Description. File Size. Download. Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 6, 8.89 KB. The Evolution of Markets 6 what is cryptography and related matters.. jce_policy-6.zip , Strong Encryption Explained: 6 Encryption Best Practices, Strong Encryption Explained: 6 Encryption Best Practices
Cryptography Attacks: 6 Types & Prevention
Algebraic Aspects of Cryptography | SpringerLink
Cryptography Attacks: 6 Types & Prevention. Best Methods in Leadership 6 what is cryptography and related matters.. Located by A cryptographic attack is a method used by hackers to target cryptographic solutions like ciphertext, encryption keys, etc., Algebraic Aspects of Cryptography | SpringerLink, Algebraic Aspects of Cryptography | SpringerLink
PSoC 6 Peripheral Driver Library: Crypto (Cryptography)

*Cryptography in Blockchain (Part 6- Blockchain Series) | by *
PSoC 6 Peripheral Driver Library: Crypto (Cryptography). Uses a common, known key to encrypt and decrypt messages (a shared secret between sender and receiver). The Evolution of Business Systems 6 what is cryptography and related matters.. An efficient method used for encrypting and decrypting , Cryptography in Blockchain (Part 6- Blockchain Series) | by , Cryptography in Blockchain (Part 6- Blockchain Series) | by
What is Cryptography? Definition, Importance, Types | Fortinet

6 Steps To Prepare For Post-Quantum Cryptography
What is Cryptography? Definition, Importance, Types | Fortinet. Top-Tier Management Practices 6 what is cryptography and related matters.. Modern cryptography techniques include algorithms and ciphers that enable the encryption PKCS #6: Extended-Certificate Syntax Standard (being replaced by X., 6 Steps To Prepare For Post-Quantum Cryptography, 6 Steps To Prepare For Post-Quantum Cryptography
6 USC 1526: Inventory of cryptographic systems; migration to post
*Theory of Cryptography: 12th International Conference, TCC 2015 *
6 USC 1526: Inventory of cryptographic systems; migration to post. The Future of Technology 6 what is cryptography and related matters.. A requirement for each agency to establish and maintain a current inventory of information technology in use by the agency that is vulnerable to decryption by , Theory of Cryptography: 12th International Conference, TCC 2015 , Theory of Cryptography: 12th International Conference, TCC 2015
Module 6 Basic Cryptography Flashcards | Quizlet

*Modern Cryptography: From Rsa to Zero-Knowledge and Beyond *
The Impact of Cross-Cultural 6 what is cryptography and related matters.. Module 6 Basic Cryptography Flashcards | Quizlet. Study with Quizlet and memorize flashcards containing terms like Which of the following hides the existence of information?, Cryptography can prevent an , Modern Cryptography: From Rsa to Zero-Knowledge and Beyond , Modern Cryptography: From Rsa to Zero-Knowledge and Beyond , MIT 6.S895 Quantum Cryptography (Spring 2024), MIT 6.S895 Quantum Cryptography (Spring 2024), To install cryptography, you will typically just run $ pip install cryptography. If you prefer to compile it yourself you’ll need to have OpenSSL installed.

